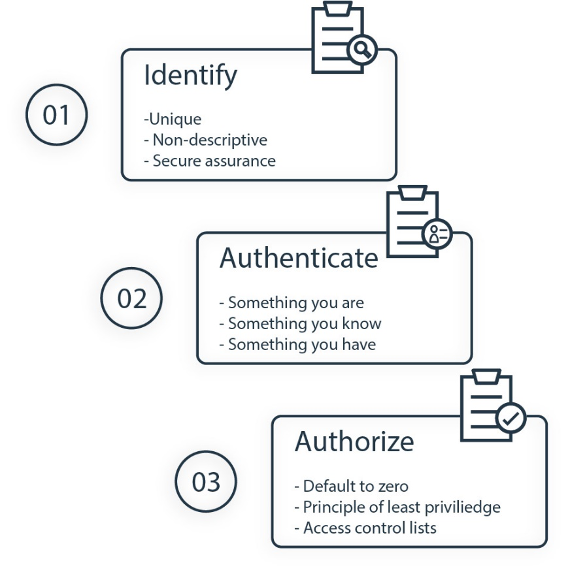
Providing access for the right people, to the right resources, at the right time starts with a well-structured identity and access management or IAM strategy; block everything else.
Identity access management or IAM defined relies on a three-step process whereby access to any resource, physical or logical, is granted only to the subject (user, program, or process) that successfully traverses each security level.