We all knew Microsoft is on a mission of world domination – but judging from this dodgy email I got the other day; I did not know that it included sanitaryware and home décor!
We all knew Microsoft is on a mission of world domination – but judging from this dodgy email I got the other day; I did not know that it included sanitaryware and home décor!
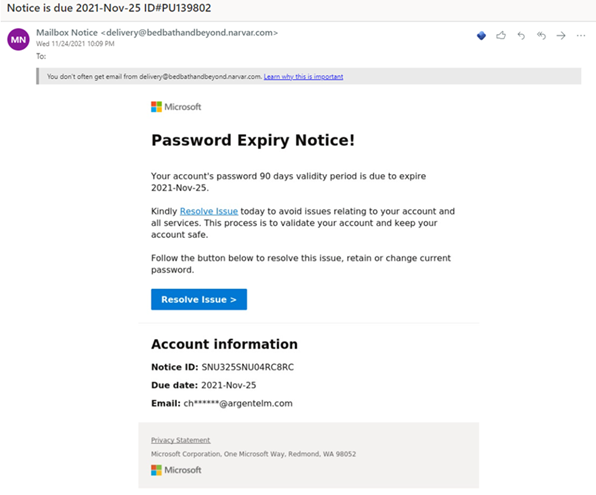
Jokes aside, how can IT professionals keep on top of the ever-evolving threat landscape, with various white and black hats competing for the ultimate prize, let alone the end-user?
Start with a Robust Cybersecurity Strategy
Yes, we are heading to machine domination; we might as well be amid one already – see our take on why you should be buying shares in tinfoil hat companies here. While this situation can provide a headache and comedic relief in one blow, protecting the end-user is becoming a real challenge.
So I thought of a suitable analogy for the end-user and reader writing this blog. The best I could come up with is that end-user protection against cybersecurity is like raising offspring, guiding, and being vigilant all the way. As development takes place, mistakes get made, achievements get celebrated, and all you can do is hope for the best. You hope that your values and beliefs have taken hold, good habits established, as at some point you will not be there should a dicey situation present itself. At this point, the values, beliefs, good habits are the ammunition you have instilled and fought tirelessly for years, are seen as empowering the end-user who could hold the fate of your organization in their hands – or at least a portion it.
So while that simmers, let’s look at what we are talking about:
Supporting peers is also key to developing excellent social skills and fostering teamwork. In the cyber world, ensure that everyone is on the same page working together, highlighting inconsistencies early. The above are vital components to ensure that end users have the right tools in the arsenal to reduce the impact of a cyber-based attack actively. COVID-19 is many things, but most importantly forced many entities to rethink their cybersecurity strategy.
A good cybersecurity strategy should include the end-users of your company. End-users can be a great asset or a huge liability. According to Tripwire, 78% of users put data at risk within organizations. They are bound to make mistakes in cyberspace but empowering them to learn from said mistakes matters. While no single article can be a silver bullet towards a holistic cyber security strategy, the following can be a starting point to achieving this.
8 Ways an End-User Can Prevent Cyber Attacks:
Recent malware attacks have targeted various companies, large and small, from healthcare to manufacturing and everything in between. Entities that do not adopt a holistic and proactive approach to cybersecurity that includes the end-user could easily find their precious data in the hands of your competitor or worse!
Identify critical assets in your company and work outwards, using a plan to document access requirements and resources needed. These could be devices, data sources, applications, and end-users. You can also read our resource here on Zero-Trust — to give you the necessary nudge to take the first step.
Conclusion
Know your users and empower them to expand your business’s security layers. A better and more secure organization will always rely on its users as an asset of the People, Process, and Technology. Please get in touch here if you need more tailored information or an overall cybersecurity solution for your workplace and empower your end-user.
Comment (01)